A Closer Look at the Work We’ve Delivered for Teams That Needed Results
Our clients love our work so much that they put their name on it. Here are some selected samples of collaborations with a few of our amazing clients.
Blogs

Bypassing MFA: Understanding the 3 Categories of Bypass Techniques
Multi-factor authentication (MFA) is viewed as a key component of modern cybersecurity, but it’s far from invincible.
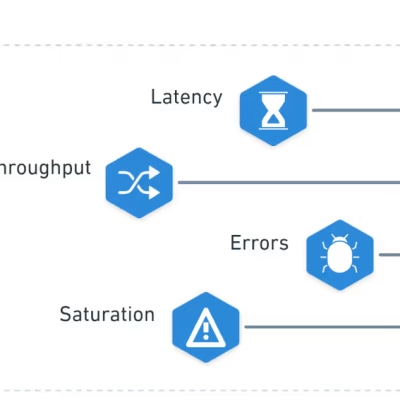
What are the 4 Golden Signals for Monitoring Kubernetes?
What do we need to consider when we monitor cloud native environments, when we need to pick the golden signals for monitoring Kubernetes
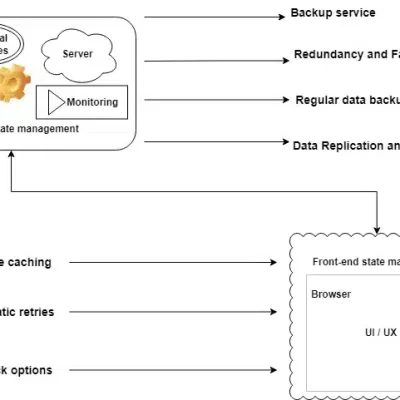
Application Disaster Recovery Best Practices
Is your team prepared for an unexpected outage? Learn the best practices of application disaster recovery for AWS cloud.
Bridging the Gap Between Observability and Automation with Causal Reasoning
Increasing visibility with observability and monitoring tools is helpful, but stopping at visibility isn’t enough.
Whitepapers/ebooks

Network and Application Observability for Multi-cloud Ops Teams
This guide focuses on observability across complex multi-cloud environments.

Disaster Recovery for Higher Education
This guide explores disaster recovery strategies tailored for higher education institutions.

Guide to EKS Cost Optimization
This guide focuses on optimizing Java applications on Kubernetes.

Ultimate Guide to Tuning Java on Kubernetes
This guide focuses on optimizing Java applications on Kubernetes.
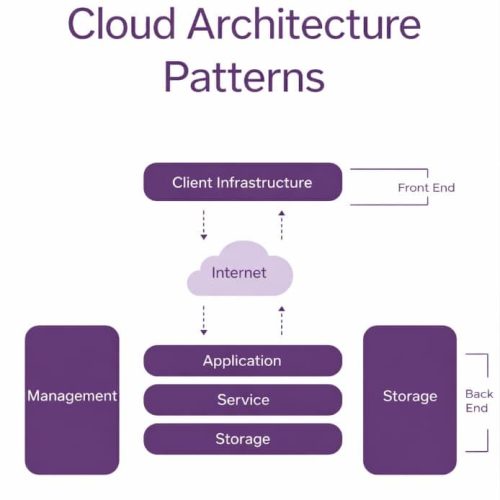
Chapter sample - OpenStack and Cloud Architecture Patterns
It explains core OpenStack components and their roles.

Building and Optimizing High-Performance SaaS Applications
This guide provides an in-depth look at designing, building, and scaling high-performance SaaS applications.
Videos & Podcasts
The GTM Delta team is fantastic to work with. They delivered content in a timely manner and it was all well written and on-message. GTM Delta is a good company to collaborate with on content generation.
